






I2P Browser | Dark Web

Description of I2P Browser | Dark Web
I2P protects your communication from dragnet surveillance and monitoring by third parties such as ISPs. This is similar to proxy apps like Tor.
But I2P is not a proxy - it is an ecosystem.
I2P is a separate anonymizing network inside the Internet. It offers a simple layer that identity-sensitive applications can use to securely communicate. All data is wrapped with several layers of encryption, and the network is both distributed and dynamic, with no trusted parties.
I2P is for users!
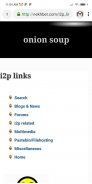
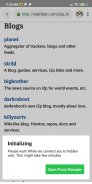
• Browse I2P eepsites: The browser configuration guide inside the I2P app will help you to start browsing websites inside I2P.
• Encrypt your emails: Bote is a high-latency encrypted email system that runs inside I2P. Get Bote: http://goo.gl/inrAHI
I2P is for developers!
• Show your users that you care about their privacy: Websites can easily be made accessible inside I2P. For more information, see the I2PTunnel documentation: https://geti2p.net/en/docs/api/i2ptunnel
• Protect your clients: Whether you are a large business or a single Android app developer, I2P can help you to secure your communications. For help with using I2P in your application, see the Application Development Guide: https://geti2p.net/en/get-involved/develop/application
























